Scope Based Recon Methodology: Exploring Tactics for Smart Recon
Reconnaissance (aka Recon) is an essential process in pentesting, especially Black Box Pentesting, where you don’t have specifics about your target. Before starting to hit your target, it is important to gather as much information as possible about your target to specify your Attack Surface area. An “Attack Surface” is a fancy term used to define the “Viable Attack Points” for your target.
Recon comes in hand when gathering information about your target. Some people may consider recon as something to automate and find vulnerabilities. However, from my experience, recon is more about crafting a better Attack Surface that will allow you to have more Attack Vectors giving you a fair opportunity to uncover potential Security Vulnerabilities.
Automation is an aspect of the recon, but the manual analysis also plays a crucial role.
In this article, I will talk about Scope Based Recon Methodology. Looking at how to perform recon and examine what methods are best to use based on your scope. Usually, it is not a good idea to apply the same type of recon to every scope; instead, it’s good to select a toolkit based on your scope and customize your recon. I’ll also discuss a few interesting tools that I use and some helpful life hacks for recon.
Let’s dig into it!
The below image outlines a detailed mindmap for Scope Based Recon Methodology (which will be the base of this article).
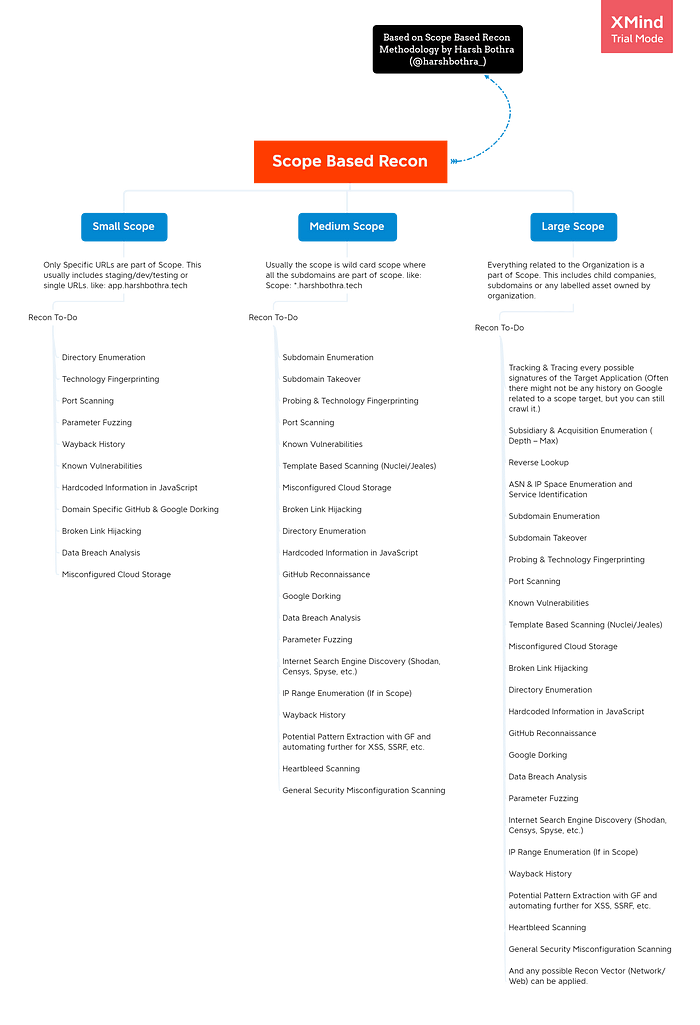
What is Scope Based Recon Methodology?
Scope Based Recon Methodology divides the recon process based on scope. Sometimes you will get a wide scope target and sometimes just a single application to work on. In such scenarios, performing the same amount of recon is less fruitful and time-consuming.
This methodology talks about what recon methods can be used for a single application vs. wildcard scope vs. wide scope.
Simply put, Scope Based Recon is a methodology to decide How to Perform Recon when a specific scope is provided.
Why Scope Based Recon Methodology is useful?
- Saves a lot of time
- You know what exactly to look for
- You can easily automate your recon workflow
- Less of a chance to submit Out-of-Scope Issues
- Just like other security methodologies, it enables you to perform better Recon
Ok, now let’s break down recon methodology by scope:
Small Scope Recon
Target Outline: Usually Single Application URL, Staging/Non-Prod/QA Environments are provided.
Example: staging-app.harshbothra.tech ; qa.harshbothra.tech ; app.harshbothra.tech ; etc.
What to Look for?
Directory Enumeration: Performing a recursive directory enumeration both with and without session is useful. Always use a good wordlist to maximum results and you will often get some good hits.
Tools & Wordlists:
- Dirsearch: https://github.com/maurosoria/dirsearch
- FFUF: https://github.com/ffuf/ffuf
- Wordlists: https://wordlists.assetnote.io/
(There are more tools & wordlist that you can use; however, these are my preferences)
Technology Fingerprinting: Check for the services running on the application. Often the servers, libraries and third-party components used might be outdated and vulnerable to known security issues.
Tools:
- Wappalyzer Plugin
- Whatweb
CVEs: Check for the CVEs and known vulnerabilities of old/outdated software and libraries used in the application.
Websites:
- https://cve.mitre.org/
- https://www.cvedetails.com/
- https://www.exploit-db.com/
- https://snyk.io/
- https://www.cybersecurity-help.cz/vdb/
Port Scanning: Performing port scanning is always useful as you can get some interesting ports exposed running some services that may be using default credentials, misconfigured, or are known vulnerable.
Tools:
Broken Link Hijacking: If the application has some social media profiles, a third party linked website, or reference to any expired domain– try to perform a takeover.
Tools:
- Broken Link Hijacking Burp Plugin: https://github.com/arbazkiraak/BurpBLH
JS Files for Hardcoded APIs & Secrets: JavaScript files often contain interesting information. Digging into each and every JavaScript file you can get a bunch of useful information from Hardcoded APIs, Secrets (such as AWS Credentials), Information about S3 Buckets, More Subdomains, PII Information, Endpoints, Interesting Parameters, Logics to Bypass certain restrictions like for XSS and Open Redirection, you can do a lot.
Now there are tons of ways to deal with JavaScript files, like:
- Use Automated tools for findings hardcoded information
- Use Automated tools for finding interesting parameters, keywords, endpoints, and other pieces of information.
- Download all JavaScript files recursively and use GF patterns/Custom Regex to look for interesting information.
- Differentiate JavaScript files (Previous vs. Current) over a period of time to see if something interesting came up.
Tools:
- SecretFinder: https://github.com/m4ll0k/SecretFinder
- JFScan: https://github.com/KathanP19/JSFScan.sh
- LinkFinder: https://github.com/GerbenJavado/LinkFinder
- DetectDynamicJS: https://github.com/PortSwigger/detect-dynamic-js (Burp Plugin)
- Retire.js: https://github.com/retirejs/retire.js/ (Burp Plugin/Browser Extension/Standalone)
- JS Link Finder: https://github.com/PortSwigger/js-link-finder (Burp Plugin)
Parameter Discovery: Often you will be able to discover parameters that might not be directly visible through the application navigation but are still processed on the server-side. These parameters are often vulnerable to attacks such as SSRF, Open Redirection, XSS, SQLi, IDORs, etc.
Tools:
- Arjun: https://github.com/s0md3v/Arjun
- ParamSpider: https://github.com/devanshbatham/ParamSpider
- Param Miner: https://github.com/PortSwigger/param-miner
Wayback History: Checking for Wayback History is always a great idea. You can often find URLs that may no longer be available through application workflow but are still accessible. Sometimes, sensitive pages are cached revealing interesting information and you can also get a bunch of endpoints to test for various different vulnerabilities.
Tools & Websites
- Wayback Machine: https://archive.org/web/
- waybackurls: https://github.com/tomnomnom/waybackurls
- gau: https://github.com/lc/gau
Domain-Specific GitHub & Google Dorking: Google Dorking methods are always useful specifically to increase the attack surface by finding more and more endpoints, exposed services, etc. However, in the case of small scope recon, you can check for authentication tokens, UUIDs, User/Asset Identifier, Backup Files, Sensitive Cached information using Google Dorks & GitHub Dorking.
Tools & Websites
- GHDB: https://www.exploit-db.com/google-hacking-database
- Interesting GitHub Dorks List: https://gist.githubusercontent.com/EdOverflow/8bd2faad513626c413b8fc6e9d955669/raw/06a0ef0fd83920d513c65767aae258ecf8382bdf/gistfile1.txt
- GitDorker: https://github.com/obheda12/GitDorker/tree/master/Dorks
- GitRob: https://github.com/michenriksen/gitrob
- GitHound: https://github.com/tillson/git-hound
Data Breach Analysis: Often you can find leaked credentials, databases, and other sensitive information of various organizations that an attacker might abuse. However, this may or may not be accepted by Bug Bounty Programs but always good to look at such things in pentesting practices.
Websites:
- Intelx: https://intelx.io/
- Hacking Forums
- Darknet/Darkweb Analysis
Misconfigured Cloud Storage: Organizations are heaving moving towards cloud infrastructure and using cloud storage options such as AWS S3 Buckets, GCP Buckets, etc. for storing their assets. However, due to simple misconfiguration, an organization can leak/reveal a bunch of a handful of information to the attackers. Always, enumerate the buckets and other cloud-based services and look for misconfiguration in them.
References:
- S3 Misconfiguration Article: https://medium.com/bugbountywriteup/s3-bucket-misconfigured-access-controls-to-critical-vulnerability-6b535e3df9a5
Medium Scope Recon
Target Outline: Usually wildcard scope is provided.
Example: *.harshbothra.tech
All the things that you do in Small Scope Recon and a few add-ons:
Subdomain Enumeration: Subdomain Enumeration doesn’t need any explanation. This is one of the starting points when dealing with wildcard and wide-scope domains. The goal is to enumerate subdomains from various resources to increase the attack surface to the maximum.
Tools:
- Subfinder: https://github.com/projectdiscovery/subfinder
- Assetfinder: https://github.com/tomnomnom/assetfinder
- Amass: https://github.com/OWASP/Amass
- Chaos: https://github.com/projectdiscovery/chaos-client
- Sudomy: https://github.com/Screetsec/Sudomy
(There are a bunch of tools available in the market, however, these are some of my preferred tools. You can always try others as per your requirements. If you configure all the required profiles in these tools, they are more than sufficient.)
Subdomain Bruteforcing: Sometimes tools miss out on multiple subdomains that may or may not be listed on various sources where these tools go and look for. Subdomain Bruteforcing helps to brute force the target’s main domain against a wordlist to see if a valid subdomain can be found. This often results in some new and fruitful subdomains, especially when there are thousands of subdomains present for a target.
Tools:
- dnsx: https://github.com/projectdiscovery/dnsx
- DNS Validator (To generate resolvers list): https://github.com/vortexau/dnsvalidator
Subdomain Takeover: Due to the misconfiguration, let’s say if your subdomain is pointing to a service X but your account/subscription is expired or you closed your account at service X but forgot to remove the pointer from your subdomain. An attacker can try to create an account on that service and add your subdomain to its account. Since the pointer is already there, it may be possible to perform a subdomain takeover.
Tools:
- Nuclei Templates
- Subdomain Takeover: https://github.com/antichown/subdomain-takeover
- Takeover: https://github.com/m4ll0k/takeover
- Osmedeus Takeover Module: https://github.com/j3ssie/Osmedeus
Probing: Once you are done enumerating and gathering subdomains from all the possible ways, the next step is to use this list of subdomains/domains and probe for working HTTP and HTTPS servers in order to filter out interesting endpoints out of the rest. You will often find out of 1000 subdomains, only 600 or so are having working HTTP/HTTPS Servers running or are reachable. This method helps you to define your attack surface in a better way.
Tools:
Template Based Scanning: This has been a game-changer in reconnaissance. Template-based scanners allow you to create a template to identify a vulnerability and re-run it on any number of targets. It works on regex and other matching patterns to check if the conditions are satisfied and if yes, it flags for that specific vulnerability. Most of the remote and unauthenticated CVEs are automated using Nuclei & Jaeles templates. It is easy to create your own templates, more information about this can be found on their GitHub Repositories.
Tools:
Internet Search Engine Discovery: Internet Search Engines (not to be confused with Google, Yahoo, Bing, etc.) are some services that monitor various internet-connected devices, services, endpoints and allows you to enumerate through them and find a bunch of misconfiguration. From penetration testing, red teaming to bug bounties, they play an important role and allows you to increase your attack surface to a greater extent.
Websites:
- Shodan: https://www.shodan.io/
- Spyse: http://spyse.com/
- Censys: https://censys.io/
- Fofa: https://fofa.so/
- BinaryEdge: https://www.binaryedge.io/
Potential Pattern Extraction with GF: Once you enumerate various URLs using waybackurls, gau, and other resources, you can use GF patterns to extract URLs that may be an interesting vector to check for specific attacks such as XSS, SSRF, SQLi, etc. You can further automate those URLs to perform automated detection of vulnerabilities while you work on them manually.
Tools:
Heartbleed Scanning: This is a well-known vulnerability found in the SSL/TLS of an application. However, seen rarely but always a good thing to check for on a larger set of targets.
Tools:
- MassBleed: https://github.com/1N3/MassBleed
General Security Misconfiguration Scanning: Apart from all of the above, you can always automate scanning for various other general misconfiguration such as:
- CORS Scanning
- Security Headers Scanning
- SPF Record Scanning
- CRLF Injection Scanning
- HTTP Request Smuggling Detection (High Chance of False Positives in Automation)
Large Scope Recon
Target Outline: Usually every single asset owned by the target organization is kept as a part of the scope.
Example: Complete Internet Presence of Harsh Bothra is part of the scope. (This will include all the assets, including subsidiaries, labels, IP ranges, etc.)
All the things that you do in Small Scope & Medium Scope Recon and few add-ons:
Tracking & Tracing every possible signature of the Target Application: In the targets which are having a huge internet presence, this step is really important. Such targets will often launch new domains, sites, campaigns and some organization also acquires other companies, opens up new baby/sister companies, etc. This helps you to track what is changing in their assets and help you be a step ahead in terms of looking for security vulnerabilities in those new assets.
Subsidiary & Acquisition Enumeration (Depth — Max): Always, Always, look for the acquisitions and subsidiaries to their maximum depth possible. For Example: If organization A owns a company B which owns company C, company C will also be a part of the scope (unless explicitly mentioned).
Websites:
- Owler: https://corp.owler.com/
- Crunchbase: https://www.crunchbase.com/
- Wikipedia & Open Google Search
Reverse Lookup: This helps you to find out more related domains and often by manually enumerating through those related domains, you can uncover domains owned by your target organization, resulting in increased scope and attack surface.
Tools & Websites:
Automated Recon Frameworks
- Project Bheem: https://github.com/harsh-bothra/Bheem
- Osmedues: https://github.com/j3ssie/Osmedeus
- ReconNote: https://github.com/0xdekster/ReconNote
Scope Based Recon Talks
Offensive & Scope Based Recon — Red Team Village c0c0n 2020
In this session, I talk about the offensive reconnaissance methodology which I implement for my pentesting and bug bounty activities. This covers scope Based Recon methodology and how to automate your recon process.
Offensive Recon — Bug Hunter’s Playbook
In this session, I talk about the Reconnaissance workflow, various tools, and the automation script which I use to automate my bug bounty Reconnaissance process. This is the point from where Project Bheem came to light.
Takeaways
- Recon is about increasing the attack surface so that you will have more attack vectors.
- Recon is not always about or equal to finding security vulnerabilities.
- Scope Based Recon helps you to automate your Recon methodology based upon various target scope (Small/Medium/Large).
- Since now you know exactly what you need to look for in the provided scope, the next step is to implement this strategy and look at the results.
- Various interesting tools and understanding why a particular methodology is useful and should be included in Recon.
- The next step is to explore and try this methodology in wild during your engagements for fun and profit altogether.
Thank you for reading this post and I hope you learned something. Feel free to drop a comment and don’t forget to check out the Scope Based Recon Mindmap here
